I am developing custom menu widget where admin can set links to any Verint content/application/container (user, group). The configuration contains the identifiers for this content (ContentId, ContentTypeId).
Using these identifiers, the widget calls the Script API and if the user does not have rights to view any content the menu item is not shown for this user.
For this, the content search function was used:
var searchItem = core_v2_searchResult.Get(contentId);
if (searchItem !== null) {
// show menu item
} else {
// hide the menu item
}
Calling this function leads to a heavy load on the search service (Solr) for the high-load community, so I am considering any other implementation option.
I am considering the following options to solve the problem:
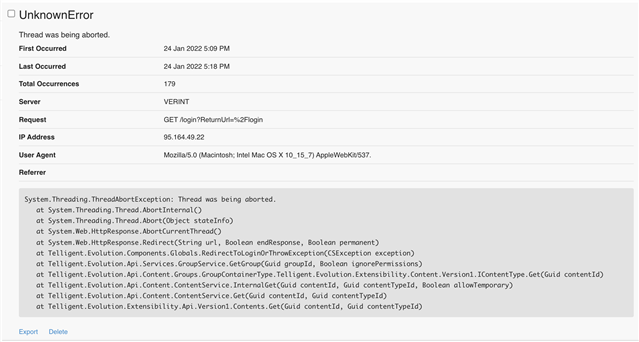
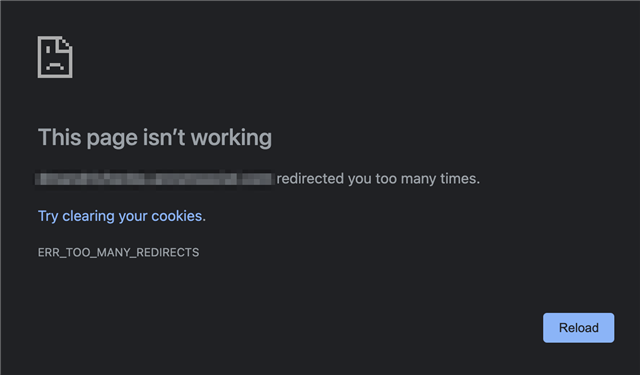
The following function call initiates an endless page reload if the user does not have permission to access the content (for example, user is a guest):
var content = core_v2_content.Get(contentId, contentTypeId);
Also, for testing, I made plugin based on IScriptedContentFragmentExtension interface, which provides its own function:
var content = se_v1_menu.GetContent(userId, contentId, contentTypeId)
A piece of code that handles access to content:
public Content GetContent (int userId, Guid contentId, Guid contentTypeId)
{
Content content = null;
var coreContents = Apis.Get<IContents>();
var coreUsers = Apis.Get<IUsers>();
try
{
coreUsers.RunAsUser(userId, () =>
{
content = coreContents.Get(contentId, contentTypeId);
});
}
catch (Exception ex)
{
// ThreadAbortException here
}
return content;
}
As with the core_v2_content.Get function, calling coreContents.Get throws a ThreadAbortException and causes the page to reload if the user does not have permission to access the content.
Is there a way to avoid this problem? Or is there another way to check permissions?
Code sample fix
[edited by: Dmitry Mandrichenko at 6:11 PM (GMT 0) on Thu, Dec 9 2021]